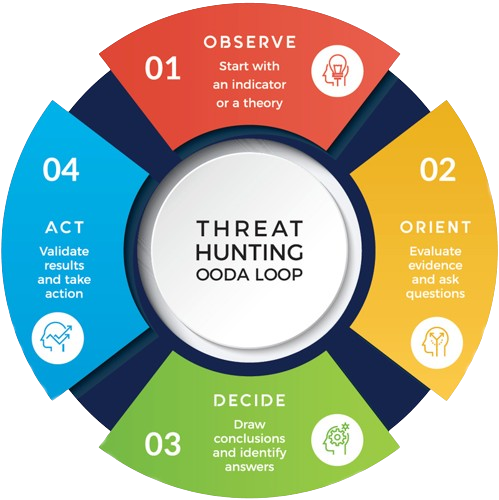
For businesses, Threat Hunting is crucial—it's like having a security guard actively searching for hidden threats to keep data safe and operations running smoothly. It's about staying ahead of cyber dangers before they become problems.
Cyber threat hunting is an active cyber defense activity. The process of proactively and iteratively searching through networks to detect and isolate advanced threats that evade existing security solutions. Our security analyst sifts through various data information using their own knowledge and familiarity with the network to create hypotheses about potential threats, such as, but not limited to, Lateral Movement by Threat Actors.
Deception Techniques
Anomaly Detection Systems
Beacons and Network Flows
Indications of Compromise
Behavioral Analysis
Tracking Tokens