In the dynamic landscape of cybersecurity, having a robust Security Operations Center (SOC) is pivotal to safeguarding your digital assets. Welcome to our SOC Operations Services, where we redefine security intelligence, incident response, and threat detection to fortify your organization against evolving cyber threats.
1. 24/7 Threat Detection and Response: Empower your organization with round-the-clock monitoring. Our SOC Operations Services ensure timely detection and rapid response to potential security incidents, minimizing the impact of cyber threats.
2. Proactive Threat Intelligence: Stay ahead in the cybersecurity game with our proactive threat intelligence services. We analyze emerging threats to provide actionable insights, allowing you to fortify your defenses before potential risks materialize.
3. Customized Incident Response: Tailor-made incident response strategies to align with your organization's unique needs. Our SOC experts work seamlessly with your team to neutralize threats and mitigate the impact of security incidents effectively.
4. Continuous Security Optimization: Evolve with the threat landscape through continuous optimization of your security measures. Our SOC Operations Services adapt to emerging risks, ensuring your security posture remains resilient over time.
Real-time Threat Detection
Rapid Incident Response
Proactive Security Measures
Comprehensive Security Analytics
Threat Intelligence Integration
Tailored Security Policies

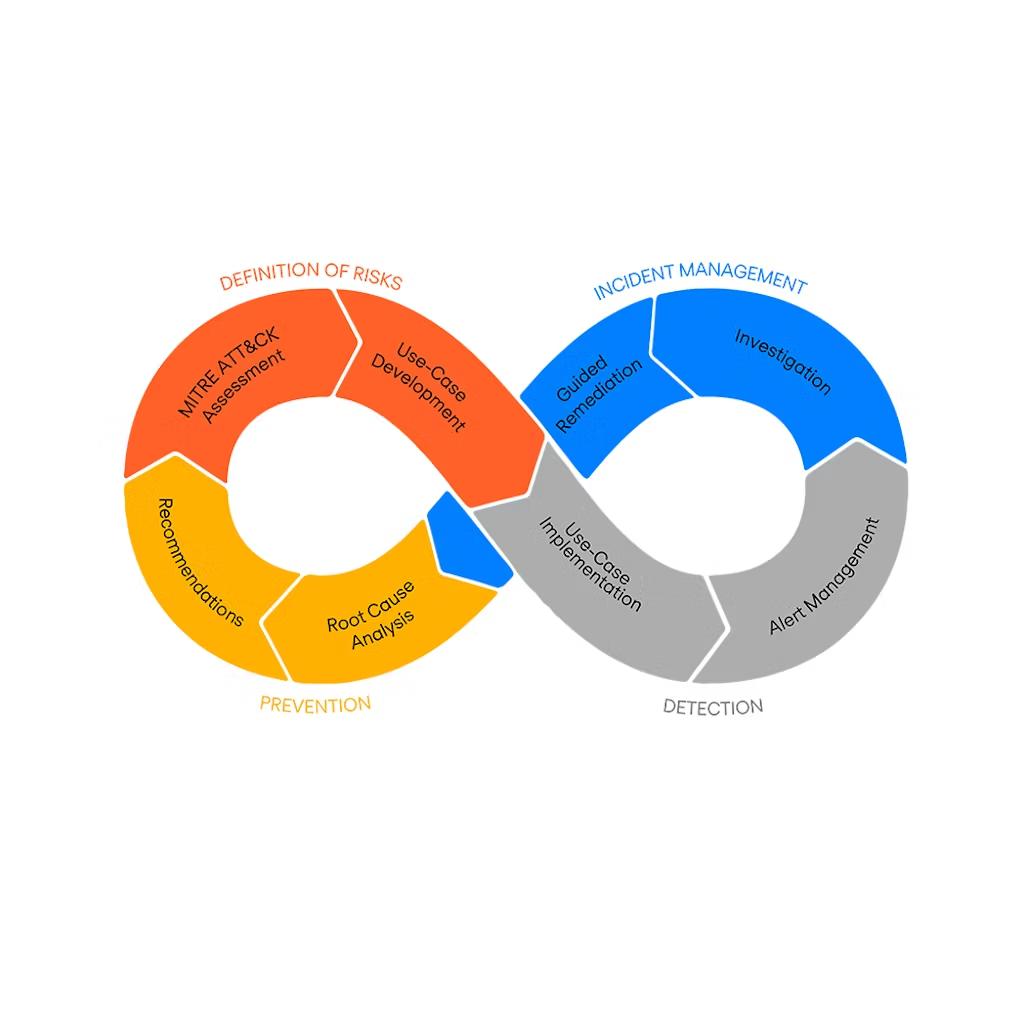
The discovery of your environment and your specificities is done through workshops covering your organisation and the personnel with whom the SOC will work.
External risk assessment, based on multiple cyber threat intelligence sources.
Internal defences: analysis of your internal security situation, including policy, security tools and organisational structure.
This step consists of the technical implementation of the use-cases in the existing security components: SIEM/XDR, EDR, NDR and SOAR.
After enriching the alerts (investigation, sandboxes), the correlation of indicators and the history of alerts known by the SOC makes it possible to refine the criticality of the alert to qualify it as an incident.
The re-evaluation of Mitre Att&ck risks and the search for root-causes allow us to propose improvement plans at each iteration of the process.
Whether you're a small business or a large enterprise, our SOC Operations Services are tailored to meet your specific security needs. Partner with us to transform your security intelligence, incident response, and threat detection into proactive, strategic advantages. Contact us today to explore how our SOC Operations Services can fortify your organization against cyber threats. Your journey to a more secure digital future starts here!